Appearance
Welcome, fellow developers and DevOps enthusiasts! 👋 In today's interconnected world, securing our deployments is paramount. Gone are the days of manual deployments and hoping for the best. We need robust, automated, and secure workflows to ensure our applications are delivered reliably and safely. This is where Advanced GitOps Workflows shine! ✨
You might already be familiar with the basics of GitOps, where Git is the single source of truth for declarative infrastructure and applications. If not, I highly recommend checking out our previous article on Understanding GitOps for Declarative Deployments to get up to speed.
Today, we're taking it a step further. We'll dive deep into advanced GitOps practices, focusing on how tools like Argo CD and FluxCD can elevate your deployment security and efficiency.
Why Advanced GitOps? 🤔
As your systems grow in complexity, so do the challenges of managing and securing them. Advanced GitOps provides solutions for:
- Enhanced Security: By treating everything as code in Git, you get an immutable audit trail of all changes. This drastically reduces the risk of unauthorized modifications and makes it easier to detect and revert malicious changes.
- Automated Compliance: Policies and security configurations can be version-controlled and automatically enforced, ensuring continuous compliance with regulatory requirements.
- Improved Reliability: Declarative configurations and automated reconciliation loops mean your production environment always matches the desired state defined in Git, minimizing configuration drift.
- Faster Recovery: In case of an incident, you can quickly revert to a known good state by simply rolling back your Git repository.
Key Principles of Secure GitOps Workflows 🔐
Repository Separation (Code vs. Configuration): It's a common best practice to separate your application code repositories from your infrastructure and configuration repositories. This separation helps in managing access control and simplifies auditing. For example:
my-app-repo: Contains your application source code.my-infra-config-repo: Contains Kubernetes manifests, Helm charts, Kustomize configurations, and other infrastructure-as-code definitions.
This ensures that changes to application logic don't directly impact infrastructure, and vice-versa, allowing for independent evolution and security patching.
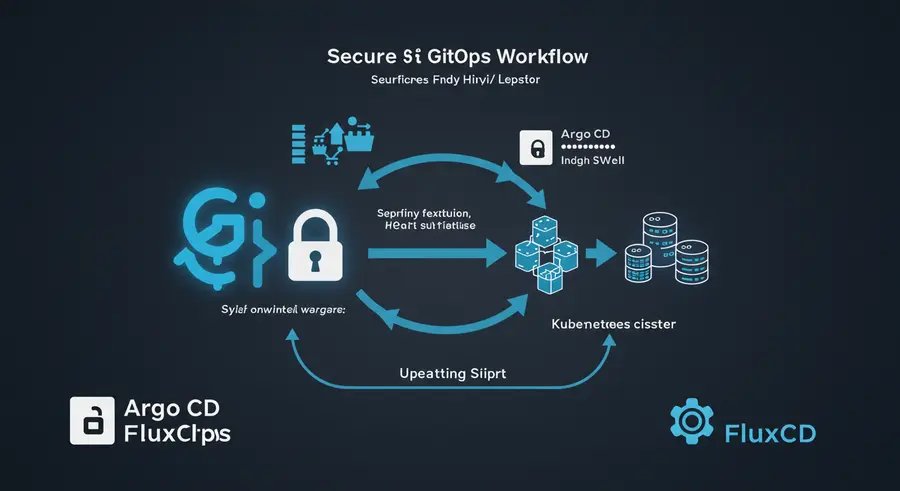
Strict Immutability: All changes to your environment should originate from Git. No manual
kubectl applycommands on the cluster! This "Git-as-the-single-source-of-truth" principle is crucial for security and auditability. GitOps operators like Argo CD and FluxCD continuously monitor your Git repositories and automatically synchronize the cluster's state with the desired state in Git.Pull-Based Deployments: Unlike traditional push-based CI/CD pipelines where the CI system pushes changes to the cluster (often requiring cluster credentials), GitOps favors a pull-based approach. The GitOps operator (Argo CD/FluxCD) runs inside your cluster and pulls changes from Git. This significantly reduces the attack surface, as the CI system doesn't need direct access to your production cluster.
yaml# Example: A simplified Argo CD Application resource apiVersion: argoproj.io/v1alpha1 kind: Application metadata: name: my-secure-app namespace: argocd spec: destination: namespace: default server: https://kubernetes.default.svc project: default source: path: deployments/my-secure-app repoURL: https://github.com/my-org/my-infra-config-repo.git targetRevision: HEAD syncPolicy: automated: prune: true selfHeal: trueIn this example, Argo CD continuously pulls from the specified Git repository and path, ensuring the
my-secure-appis always in sync.Least Privilege Principle: Apply the principle of least privilege to your GitOps tools and their interactions.
- Git Repository Access: Only authorized personnel and automated systems (like your GitOps operator) should have write access to your configuration repositories.
- Kubernetes RBAC for Operators: Configure your GitOps operator with the minimum necessary Kubernetes Role-Based Access Control (RBAC) permissions to manage the resources it's responsible for.
Auditability and Traceability: Every change in your Git repository is a commit, providing a clear history of who changed what, when, and why. This inherent audit trail is invaluable for security investigations, compliance audits, and debugging.
Advanced Tooling: Argo CD and FluxCD 🛠️
Both Argo CD and FluxCD are powerful, CNCF-graduated projects that implement GitOps principles for Kubernetes. While they share core functionalities, they have distinct philosophies and features that can be leveraged for advanced secure workflows.
Argo CD
Argo CD is known for its user-friendly UI, making it easy to visualize and manage applications, monitor synchronization status, and perform manual syncs/rollbacks (though automation is preferred).
Advanced Security Features with Argo CD:
- ApplicationSets: Manage applications across multiple clusters and environments from a single Git repository. This ensures consistent security configurations across your entire fleet.
- Sync Waves and Hooks: Control the order of resource deployments and execute pre/post-sync tasks, allowing for complex deployment strategies and integration with security scanning tools.
- RBAC Integration: Fine-grained access control within Argo CD, allowing you to define who can access and manage specific applications or projects.
- Drift Detection and Remediation: Argo CD continuously monitors the live state of your applications against the desired state in Git. If any drift is detected (e.g., a manual change on the cluster), it can automatically remediate it by syncing back to the Git state, preventing unauthorized tampering.
FluxCD
FluxCD takes a more Kubernetes-native and Git-centric approach, emphasizing automation and extensibility through a collection of specialized tools (toolkits).
Advanced Security Features with FluxCD:
- Source Controllers: FluxCD's modular design allows it to pull from various sources (Git, Helm repositories, S3 buckets), with built-in support for secure access using Kubernetes secrets.
- Kustomize and Helm Controllers: These controllers manage your Kubernetes manifests and Helm releases directly from Git, ensuring all configurations are version-controlled.
- Image Automation: FluxCD can automatically detect new container image tags in a registry and update your Git repository with the new tags, triggering a deployment. This can be integrated with image scanning tools to ensure only secure images are deployed.
- Notification Controller: Get alerts on successful deployments, failures, or security-related events, enabling proactive security monitoring.
- Multi-tenancy: FluxCD supports multi-tenant setups, allowing you to isolate different teams or projects within the same cluster with distinct GitOps configurations and permissions.
Practical Tips for a More Secure GitOps Implementation 💡
- Sign Your Commits: Use GPG to sign your Git commits. This verifies the identity of the committer and ensures the integrity of your configuration, preventing spoofing.
- Enforce Branch Protection Rules: On your Git platform (GitHub, GitLab, Bitbucket), enforce branch protection rules for your configuration repositories. Require pull request reviews, status checks (e.g., security scans, linting), and restrict direct pushes to main branches.
- Integrate Security Scans in CI/CD: Before merging changes to your GitOps configuration repository, run security scans (SAST, DAST, IaC scanning) on the proposed changes. This "shift-left" security approach catches vulnerabilities early.
- Secrets Management: Never commit sensitive information (API keys, passwords) directly to Git. Use a dedicated secrets management solution like HashiCorp Vault, Kubernetes Secrets with encryption (e.g., Sealed Secrets), or cloud-native secret managers (AWS Secrets Manager, Azure Key Vault, Google Secret Manager). Your GitOps operator can then pull these secrets securely.
- Regular Audits and Reviews: Periodically review your GitOps configurations, access permissions, and audit logs to ensure adherence to security policies and best practices.
Conclusion 🎉
Advanced GitOps workflows, powered by robust tools like Argo CD and FluxCD, are not just about efficient deployments; they are about building a more secure and resilient software delivery pipeline. By embracing principles of immutability, pull-based deployments, least privilege, and comprehensive auditability, you can significantly harden your systems against threats and ensure that your applications are delivered with confidence.
Embrace the GitOps revolution, secure your deployments, and happy coding! 🚀